Information Security Management Mission
To effectively implement the ISO/IEC 27001 Information Security Management System (ISMS), Ichia Technologies adopts a systematic management approach as its core, integrating process and policy development, regulatory compliance, education and training, and the application of information technologies. Through these efforts, the Company continuously strengthens the overall security protection capabilities for data, information systems, equipment, and network communications. Furthermore, by adopting a risk-based management mechanism, Ichia Technologies proactively identifies and controls risks arising from human error, malicious activities, system failures, or natural disasters that may lead to unauthorized access, improper use, disclosure, alteration, or destruction of information assets. Relevant protective measures are regularly reviewed and continuously improved. Through sound information security governance and a continuous improvement mechanism, Ichia Technologies is committed to maintaining the confidentiality, integrity, and availability of its information assets, fulfilling its responsibilities to shareholders, customers, and other stakeholders, and ensuring business continuity, operational stability, and service reliability.
International Standards Certification
Ichia Technologies has obtained ISO/IEC 27001:2022 certification and has established and maintained an Information Security Management System (ISMS) in accordance with ISO/IEC 27001. The scope of management includes, but is not limited to, the following:
(I) Management Framework
- Information Asset Management
- Access Control and Account Management
- Information Security Risk Assessment and Treatment
- Information Security Incident Reporting and Response
- Management Review and Internal Audit
(II) Specific Management Measures
- Regularly conduct information security risk assessments and vulnerability scans, and track remediation effectiveness
- Implement a multi-layered defense mechanism (firewalls, antivirus solutions, and endpoint protection)
- Establish information security incident reporting and response procedures
- Strengthen account management and multi-factor authentication mechanisms
- Regularly conduct information security awareness and education training
Information Security Risk Management Framework
An information security management organization has been established, with a Chief Information Security Officer (CISO) appointed to oversee the planning and implementation of information and cybersecurity management activities. In addition, an Information Security Management Committee has been formed to review information security policies, supervise risk management, and make decisions on significant information security matters. The implementation status of information security policies, results of internal audits and management reviews, as well as related corrective and improvement measures, are incorporated into management review agendas and reported regularly to senior management to ensure the continuous and effective operation of the information and cybersecurity management framework.
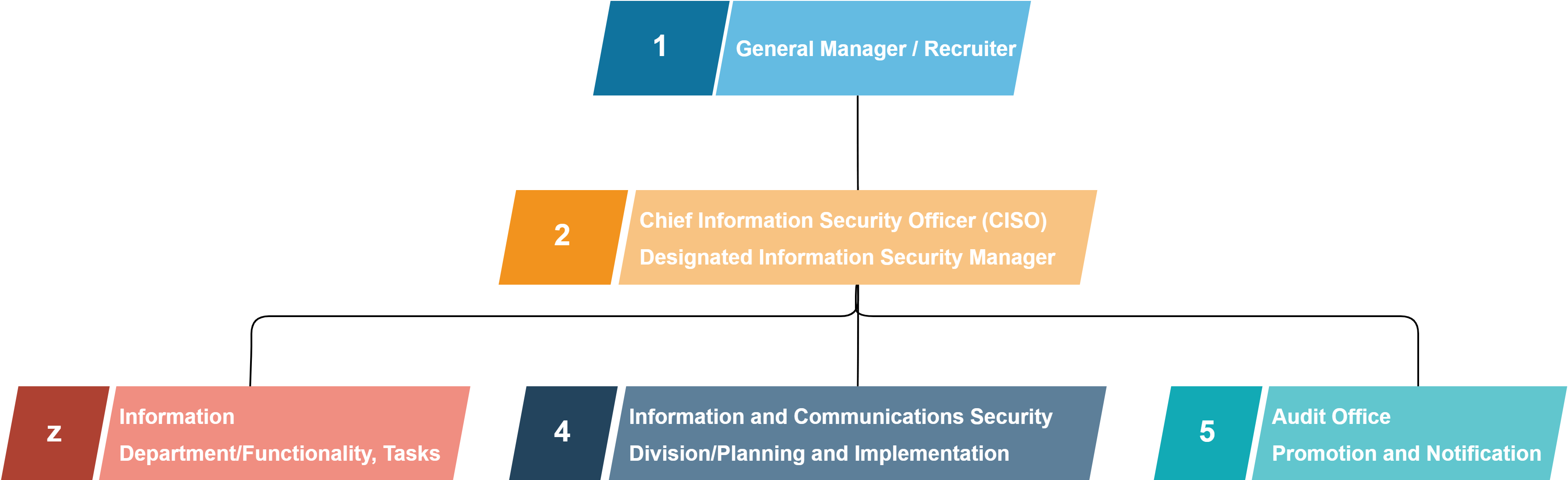
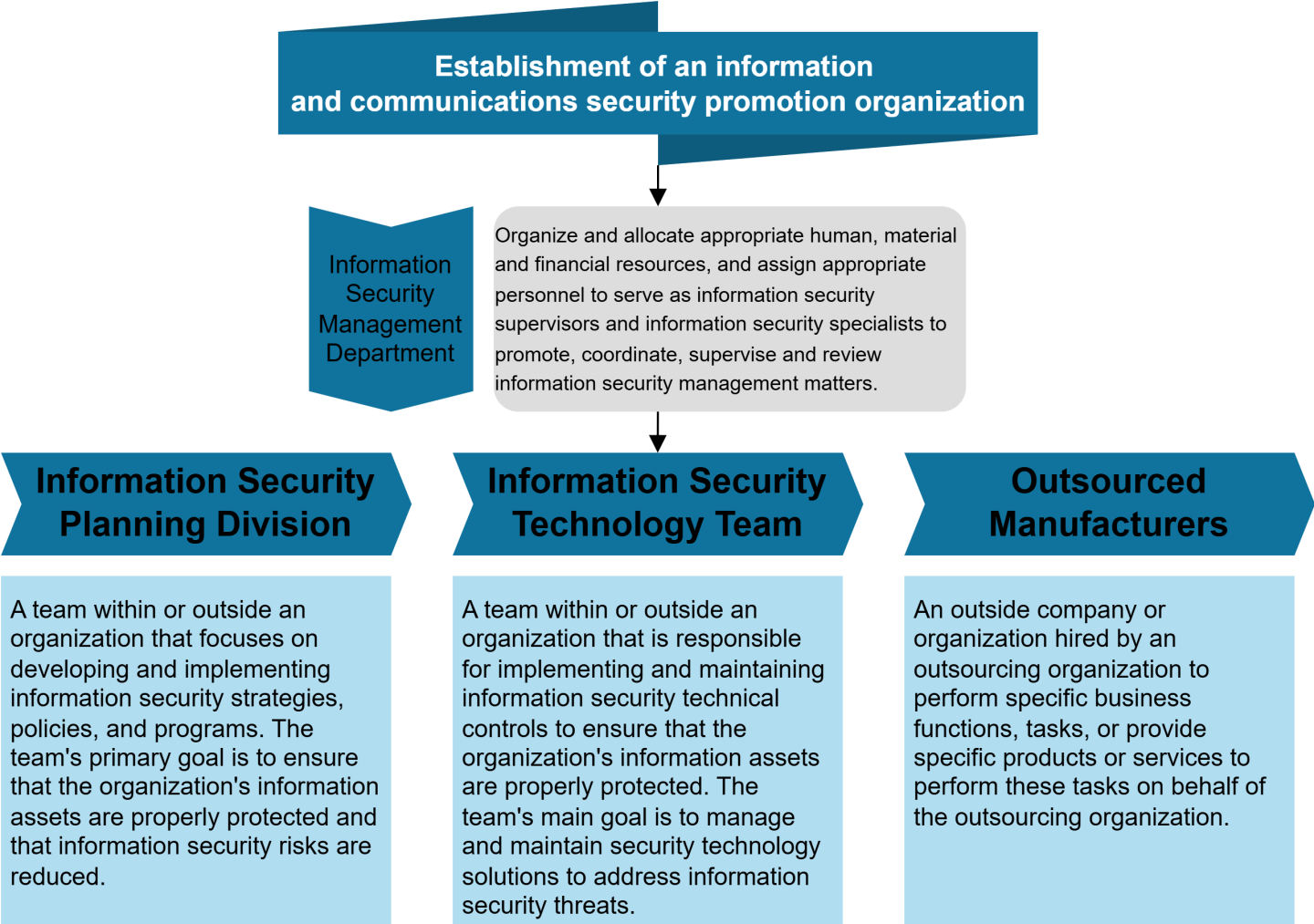
Information Security Policies and Management System
Information security policies and related information and cybersecurity management procedures have been established and implemented, covering areas such as risk assessment, access control, human resource security, outsourced service management, information security incident reporting, and business continuity management. These policies and procedures are reviewed and revised periodically in accordance with management requirements to ensure the completeness and appropriateness of the information security management system. In addition, the Company regularly collects and analyzes the latest cybersecurity threat intelligence through the official information security intelligence sharing mechanism, TW-ISAC (Taiwan Information Security Information Sharing and Analysis Center).
Integration of the NIST CSF Framework with the PDCA Management Mechanism
With reference to the NIST Cybersecurity Framework (CSF), an information and cybersecurity management approach covering Identify, Protect, Detect, Respond, and Recover has been established. This approach is integrated with the ISO/IEC 27001 Information Security Management System and serves as a key basis for information and cybersecurity governance and risk management, with the aim of continuously enhancing overall cybersecurity protection capabilities.
- In accordance with risk-based principles, information security risk assessments are conducted on a regular basis, and business continuity and disaster recovery drills are planned and implemented to enhance response and recovery capabilities in the event of cybersecurity incidents or unexpected disruptions.
- Cybersecurity risk treatment measures include not only risk reduction through policies, procedures, and technical controls, but also the evaluation of cybersecurity insurance as one of the risk transfer mechanisms, in order to mitigate potential operational and financial impacts arising from major cybersecurity incidents.
- With respect to personnel management, information and cybersecurity education, training, and awareness programs are planned in accordance with job roles and operational requirements, strengthening the cybersecurity awareness and professional capabilities of governance, management, and technical personnel, and ensuring the effective implementation of the information and cybersecurity management system.
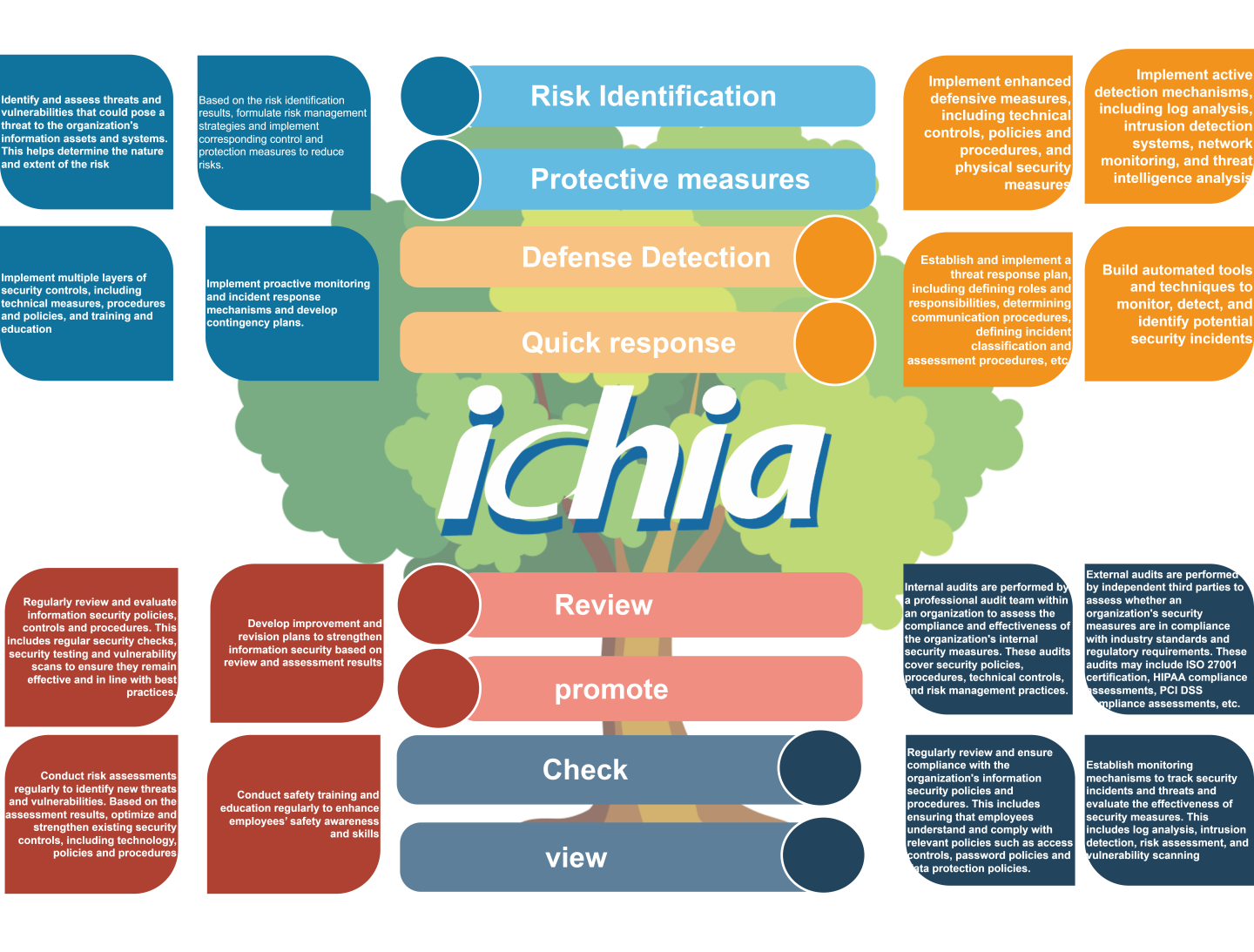
Information and Cybersecurity Risks and Mitigation Measures
In response to the increasing severity of cyberattacks and data breach risks, Ichia Technologies continues to strengthen its cybersecurity protection framework. Through systematic management, technical safeguards, and education and training, the Company aims to mitigate the impact of information security incidents on its operations and corporate reputation.
| Key Risks | Potential Impact | Mitigation Measures |
|---|---|---|
| Malware and Ransomware Attacks | System Disruption and Operational Impact | Endpoint protection, antivirus solutions, backup mechanisms, and regular drills |
| Account Compromise | Unauthorized Access | Multi-factor authentication and password policies |
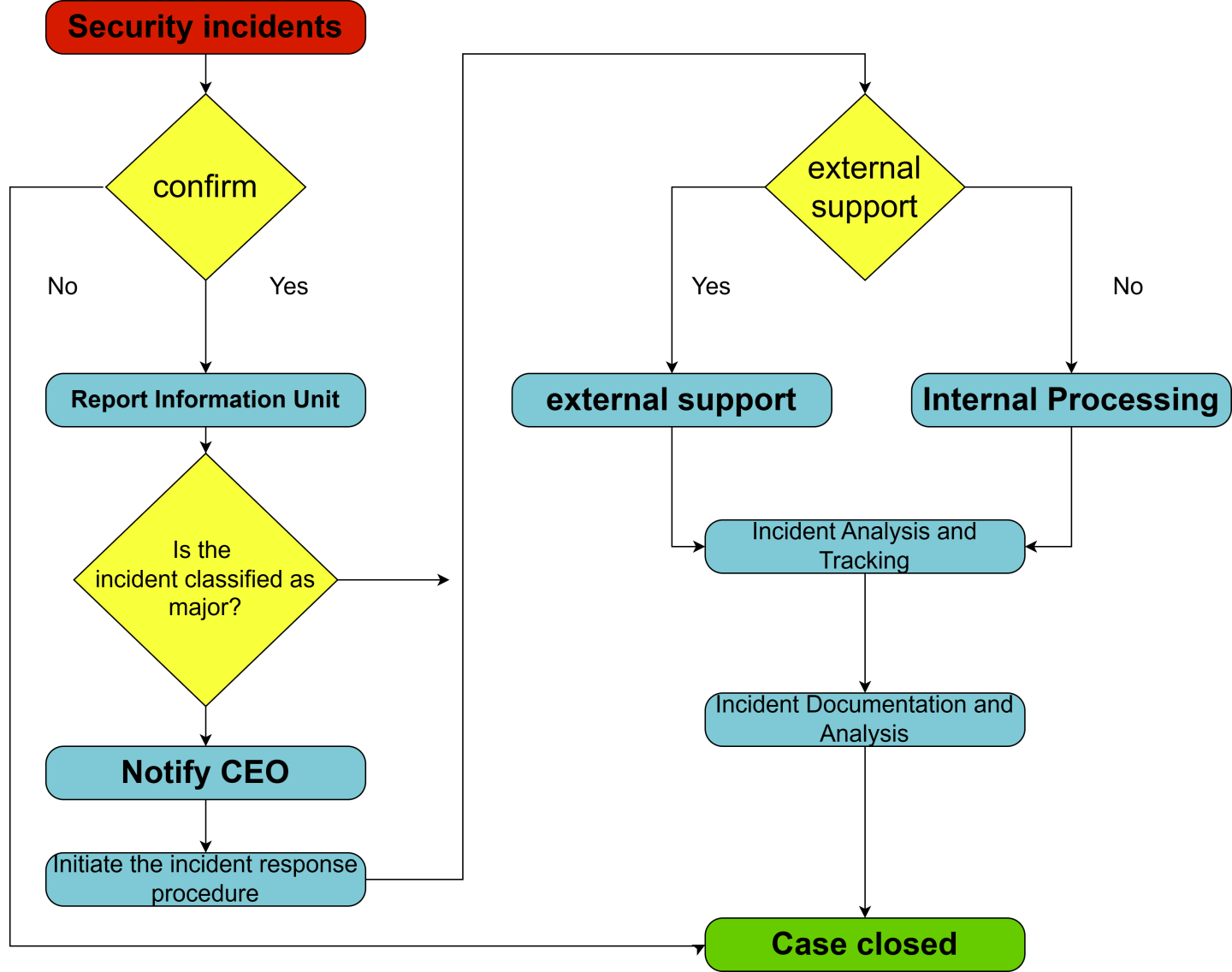
Information Security Incident Reporting and Response
In the event of an information security incident, reporting and response actions will be initiated in accordance with established management mechanisms. Through timely handling and continuous improvement, the Company aims to minimize the impact on its operations.
Education, Training, and Awareness
| Date | Course Content | Training Duration | Participants |
|---|---|---|---|
| December 2025 | Information Security Awareness Training | 180 Minutes | All Employees |
| September 2025 | Personal Data Protection | 180 Minutes | All Employees |
| June 2025 | Cybersecurity Awareness Program | 180 Minutes | All Employees |
Major Information and Cybersecurity Incidents
| Year | Data Breach Incidents (Cases) | Incidents Involving Customer Personal Data | Major Information Security Incidents |
|---|---|---|---|
| 2025 | 0 | 0 | 0 |
| 2024 | 0 | 0 | 0 |
| 2023 | 0 | 0 | 0 |


